
A hackerek már a nappaliban vannak – SmartHomeExpo’21 (HU)
2021-02-18
Trend-idők: Okosotthonok jövője – Kossuth Rádió
2021-06-07Paranoia is the secret to longevity
“Paranoia is the secret to longevity” (Vavyan Fable, The Bone Flute) is not only true in the world of crime fiction (Fable’s book follows a modern cat burglar working online, targeting everyone from individuals to banks and multinational companies) but also true to life.
The cheapest and clearly the most effective solution is to simply be vigilant but there are also thousands of ways to protect ourselves against attacks. So, let’s look at the most common data phishing methods and possible forms of protection.Protection against data phishing is now a widely discussed subject, continuous news about hacked accounts and the unstoppable leakage of data from big tech companies clearly shows that something is still amiss. A glance at a some telling numbers is enough to verify this statement: over the last two years alone the data of 250 million users has been stolen from Microsoft systems, 330 million from Twitter and 420 million from Facebook accounts, to name but a few of the biggest names. Furthermore, it is rather revealing that so far, in 2020, a fine of €50m has been imposed on Google for the breach of GDPR regulations, over €35m on H&M, nearly €28m on telecommunications service provider TIM, €22m on British Airways and €18m on Austrian Post.
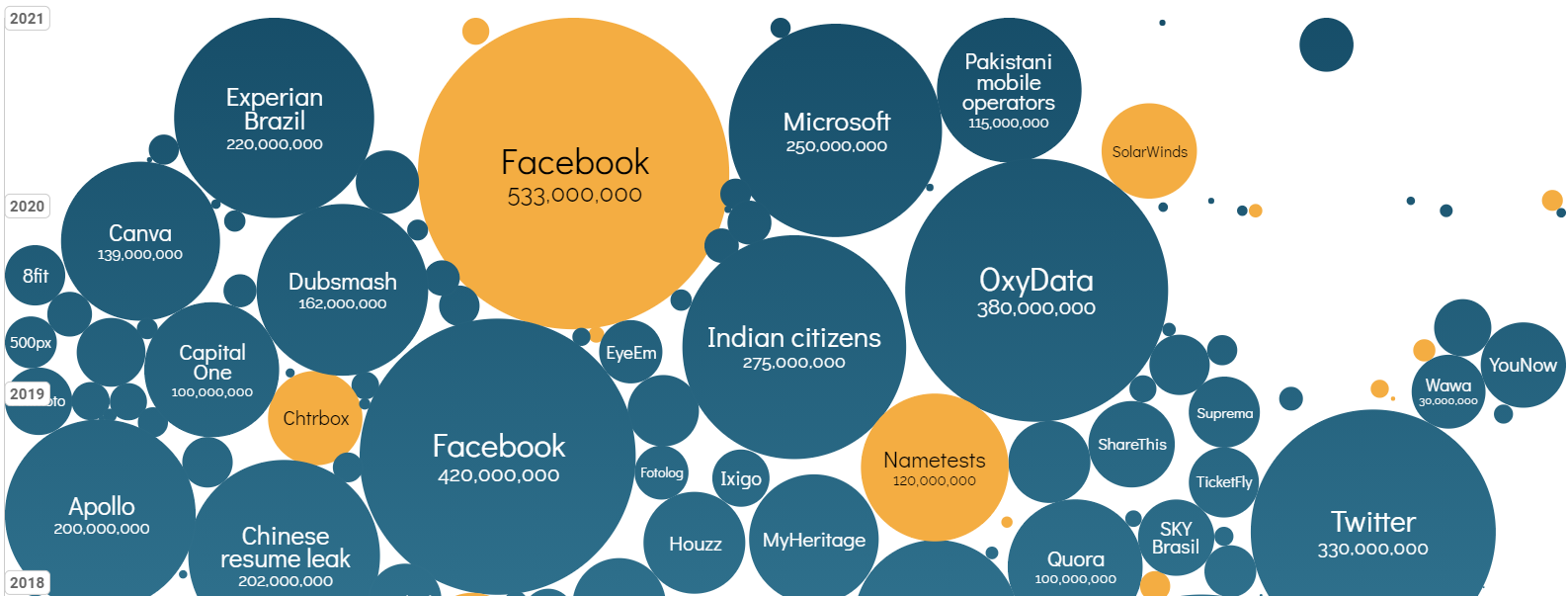
World's BiggestData Breaches & Hacks (www.informationisbeautiful.net)
The little fish are going after the big fish
One might think that large companies already have reliable protection in order to avoid the likes of above-mentioned instances, yet reality shows that the situation is exactly the opposite. Individual users are most often targeted by hackers, and the more users that work at a company, the more likely it is for someone to accidentally take the bait. The cyber espionage campaign ‘Operation Cloud Hopper’ is a famous example of this method which initially was mainly focused on Asian corporations, but now also targets numerous large companies across the globe.
The method revolves around a technique known as “spear phishing”, which is based on the idea that one of the large numbers of targeted employees will likely be careless enough to click on a link sent via e-mail or provide their password. If a hacker manages to get hold of the key data of a user, they will practically have free access to the mail server, allowing them to get to the system administrator. If this succeeds, the door will be open to the company’s internal systems, allowing them to release valuable data using various techniques.
You’ve inherited 950 billion dollars, just click here
Since it’s clear that most grand-scale data phishing schemes are based on the vulnerability of individual users, together with my colleague, doctoral candidate Barnabás Sándor, we prepared a study to specifically survey techniques developed for this purpose. In order to receive as much scam e-mail as possible, we intentionally set out to make all the possible mistakes in online data protection. We responded to letters from spammers, made our phone number and e-mail address publicly available and subscribed to publicly available newsletters. By reconstructing the typical mistakes of users, we made ourselves the perfect target for spam and phishing campaigns.
The pressure various phishing e-mails or unsolicited content put on the average user is constant: Kaspersky’s survey showing the share of spam in the overall volume of e-mails provides an interesting overview on the subject. Based on this, it’s safe to say that even in milder months, the share of spam in the e-mail traffic of a common user is barely below 50 percent. Therefore, there’s a substantial likelihood that someone will carelessly expose themselves to a data breach attempt.
One might think that large companies already have reliable protection in order to avoid the likes of above-mentioned instances, yet reality shows that the situation is exactly the opposite. Individual users are most often targeted by hackers, and the more users that work at a company, the more likely it is for someone to accidentally take the bait. The cyber espionage campaign ‘Operation Cloud Hopper’ is a famous example of this method which initially was mainly focused on Asian corporations, but now also targets numerous large companies across the globe.
The method revolves around a technique known as “spear phishing”, which is based on the idea that one of the large numbers of targeted employees will likely be careless enough to click on a link sent via e-mail or provide their password. If a hacker manages to get hold of the key data of a user, they will practically have free access to the mail server, allowing them to get to the system administrator. If this succeeds, the door will be open to the company’s internal systems, allowing them to release valuable data using various techniques.
You’ve inherited 950 billion dollars, just click here
Since it’s clear that most grand-scale data phishing schemes are based on the vulnerability of individual users, together with my colleague, doctoral candidate Barnabás Sándor, we prepared a study to specifically survey techniques developed for this purpose. In order to receive as much scam e-mail as possible, we intentionally set out to make all the possible mistakes in online data protection. We responded to letters from spammers, made our phone number and e-mail address publicly available and subscribed to publicly available newsletters. By reconstructing the typical mistakes of users, we made ourselves the perfect target for spam and phishing campaigns.
The pressure various phishing e-mails or unsolicited content put on the average user is constant: Kaspersky’s survey showing the share of spam in the overall volume of e-mails provides an interesting overview on the subject. Based on this, it’s safe to say that even in milder months, the share of spam in the e-mail traffic of a common user is barely below 50 percent. Therefore, there’s a substantial likelihood that someone will carelessly expose themselves to a data breach attempt.
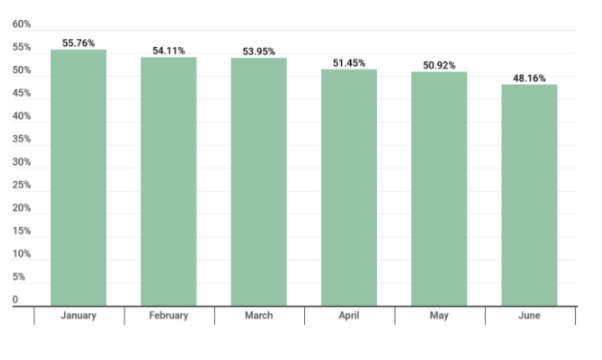
Share of spam in e-mail traffic –Kaspersky, 2021
Oddly enough, it was relatively hard for us to encounter a major cyber-attack during our research. It took days to receive the first data phishing e-mail and the initial messages took a rather primitive approach. E-mails like this usually contain an image with some ridiculous message, in which the sender promises to forward something like 950 billion US dollars to us if we give them our data. The other similarly worded e-mail claimed that they breached our account, allowing them to access all our passwords and they even had some video recordings of our racy sexual “activities” performed in front of the webcam. Not only was the blackmailing attempt ridiculous because we obviously did nothing racy in front of the webcam, but because it was obvious to us that they didn’t hack into our system and had no passwords whatsoever.
In a somewhat more skillful attempt,we received a phone call from London, during which the caller (who had a heavy foreign accent) introduced himself as a Microsoft customer service representative. The story was that their system indicated to them that Windows had been reinstalled, and since this took place, our system was continuously issuing error messages. In order to back up this claim, the caller asked us to open the Event Viewer application on our computer running Windows and click on the “Custom Views/Administrative Events” tab, where we could see that there’s something wrong with our device. Note to the reader: it’s entirely natural for users to see yellow and red exclamation marks under this tab.
In a somewhat more skillful attempt,we received a phone call from London, during which the caller (who had a heavy foreign accent) introduced himself as a Microsoft customer service representative. The story was that their system indicated to them that Windows had been reinstalled, and since this took place, our system was continuously issuing error messages. In order to back up this claim, the caller asked us to open the Event Viewer application on our computer running Windows and click on the “Custom Views/Administrative Events” tab, where we could see that there’s something wrong with our device. Note to the reader: it’s entirely natural for users to see yellow and red exclamation marks under this tab.
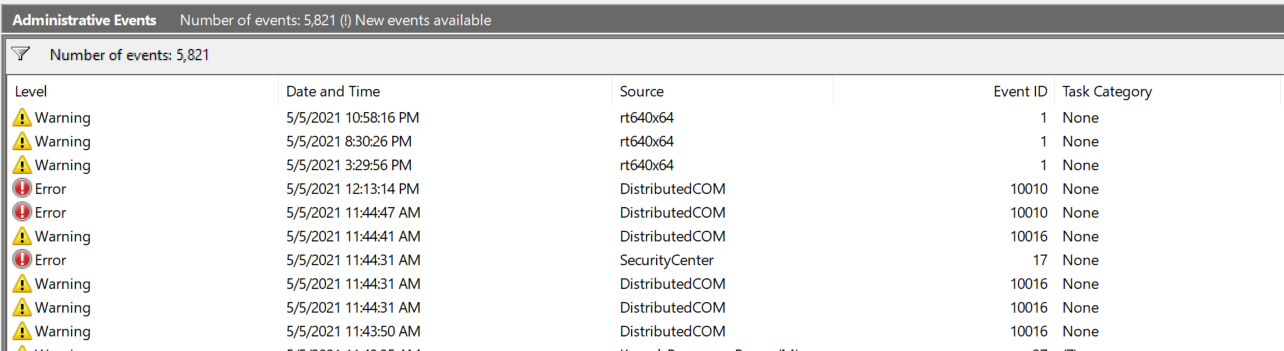
Windows Event Log
In the end, the attempt failed when we asked the representative from London to send us a confirmation e-mail before we provided our data and they simply hung up. To a certain extent, the scams based on the idea of sending letters on behalf of postal delivery services were similar to this approach. These messages most often claim that they couldn’t deliver a parcel, asking the user to click on a link to update their data. Naturally, the link is a cover for some clever little application, such as a Lokibot installer.
Let’s equip ourselves!
For the sake of brevity, I won’t go into all the typical types of scams, but I feel it’s important to talk about protection as well. Even if someone isn’t specialised in the field of cyber security and doesn’t want to spend money on various security services, they still don’t have to be concerned about being vulnerable. OSINT (Open-Source Intelligence) applications can help, you can choose the most effective device from the following list, based on your current needs.
Protection doesn’t start with the use of these sites, but rather by boosting the consciousness of users. It’s good to keep in mind that there are a range of tools at our disposal to skillfully inquire about an e-mail, attachment or website that looks like a scam. All of the above-listed applications are free, so they can be used practically any time when we have to deal with a security-related issue. Despite being free, these applications don’t hinder work at all; they offer all the key functions one could hope for. Finally, keep in mind that no security technology can be truly effective if the operators of the system don’t have up-to-date knowledge on the latest methods of attacks, breaches and campaigns so it’s important for us to demand the same degree of conscious use from ourselves as we do from others.
Szerző: Dávid János, FEHÉR
Source
Let’s equip ourselves!
For the sake of brevity, I won’t go into all the typical types of scams, but I feel it’s important to talk about protection as well. Even if someone isn’t specialised in the field of cyber security and doesn’t want to spend money on various security services, they still don’t have to be concerned about being vulnerable. OSINT (Open-Source Intelligence) applications can help, you can choose the most effective device from the following list, based on your current needs.
- virustotal.com is a universal, one-stop-shop website, offering a range of important services. Users can analyse URLs through the site, upload suspicious files and run tests on practically all major antivirus software. The site can also manage hash-identifiers, allowing you to check whether a specific identifier is listed in any of the major antivirus definition databases.
- IBM X-Force exchange can be used to inquire about suspicious URLs and IP-address related reports. The site is incredibly effective at collecting the characteristics of previous suspicious activities on websites. It indicates, for example, if a website or the IP address, is currently or previously involved in the spread of a virus or whether other malicious activities are conducted through the site.
- Urlscan.io helps examine the contents of a URL without loading it on your device, allowing you to check its contents, find out where and who site is registered to, as well as identify the IPs addresses of the site.
- Whois.Domaintools provides a great deal of information on the registration dates and operators of websites. This can help handle cases where someone claims to be acting on behalf of Telekom or Facebook, while directing you to a site that isn’t registered to Telekom or Facebook via e-mail.
Protection doesn’t start with the use of these sites, but rather by boosting the consciousness of users. It’s good to keep in mind that there are a range of tools at our disposal to skillfully inquire about an e-mail, attachment or website that looks like a scam. All of the above-listed applications are free, so they can be used practically any time when we have to deal with a security-related issue. Despite being free, these applications don’t hinder work at all; they offer all the key functions one could hope for. Finally, keep in mind that no security technology can be truly effective if the operators of the system don’t have up-to-date knowledge on the latest methods of attacks, breaches and campaigns so it’s important for us to demand the same degree of conscious use from ourselves as we do from others.
Szerző: Dávid János, FEHÉR
Source




